One third of phishing pages cease to be active after a day

The first hours of a page's life the most dangerous for users - according to Kaspersky's latest findings. This is the moment when a vast range of phishing links are spread before the site is detected and entered into databases by anti-phishing engines.
Threats are numerous but short-lived
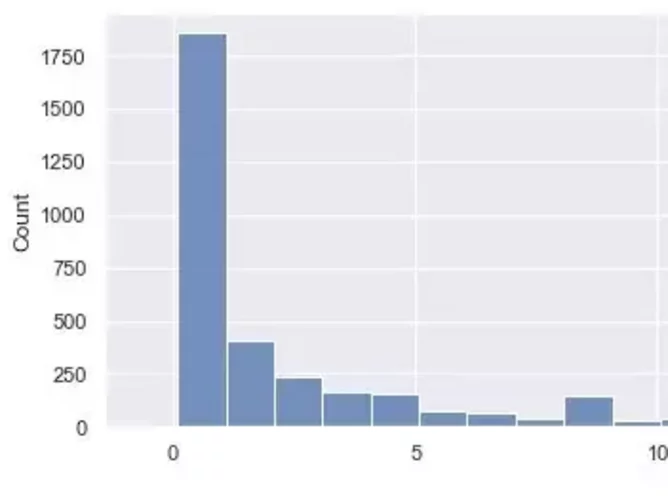
Researchers analysed 5307 examples of phishing pages between July 19 to August 2, 2021, finding that nearly 2000 links stopped being active after the first day of monitoring.
Numerous pages ceased to exist in the initial first hours, meaning that as early as 13 hours after monitoring, a quarter of all pages were inactive. Half of the pages lived no more than 94 hours.
Advanced phishing tactics can be stopped
Opportunistic phishers are interested in distributing links to phishing pages as soon as they are created, to ensure the widest possible reach to potential victims in the first hours while their sites are still active. As soon as site administrators see a phishing page, they remove it and it can be logged in anti-phishing databases.
Even if phishers have deployed their own server on the purchased domain and are suspected of fraudulent activity, the registrars may deprive the phishers of the right to host the data on it.
Much more often, attackers choose to create a new page instead of modifying an existing one.
Another tactic is creating randomly generated code elements that are not visible to the user, but still prevent anti-phishing engines from blocking them for an uncertain amount of time. Kaspersky claim that their anti-phishing engine skillfully bypasses such tricks.
Content modifications often mimic the 'PUBG' giveaway, one of the most well-known events of the popular online game. Attackers change the content of the page in a timely manner to match the new season, a temporary event in the game, or to make the phishing page resemble the original as closely as possible.
“Such research is not only useful for updating our databases, but it can also be used to improve incident response. For example, if an organisation is undergoing a spam attack with fraudulent links, it's important to repel it in the first hours, as it’s the most beneficial time for phishers’ activity. In turn, it is important for users to remember that when they receive a link and have doubts about the legitimacy of the site, we recommend they wait for a few hours. During that time, not only will the likelihood of getting the link in the anti-phishing databases increase, but the phishing page itself can stop its activity. Users can rest assured that they are well protected, since we not only catch phishing, but also conduct research to improve how well we repel attacks”, comments Egor Bubnov, security researcher at Kaspersky.
- Employees can help prevent phishing attacks, say BlackBerryCloud & Cybersecurity
- 5 mins with Tom Kellermann, cyber security leader at VMwareCloud & Cybersecurity
- Exec Q&A with Stephen de Vries, IriusRisk CEO and co-founderCloud & Cybersecurity
- Open Systems appoints new Chief People Officer, Alaska MayCloud & Cybersecurity






